Computer surety is an increasingly authoritative considerateness . From certification to encryption key , learn how to keep your electronic computer ’s hard drive protected and your personal info safe .
matter to search :
Avoid the Most Common Passwords With These Security Tips
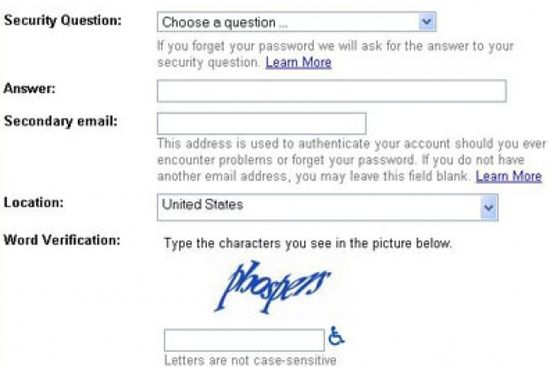
How CAPTCHA Works
What is a digital signature?
Top 6 Privacy and Security Apps to Safeguard Your Digital Life
3 Essential Steps for Mobile Privacy With Startpage
Top Private Search Engines: Comparing 5 Competitors
10 Worst Computer Viruses of All Time
9 Things Everyone Should Know About The Hacktivist Group Anonymous
How Trojan Horses knead
Can the Government See Which Websites I Visit ?
Learn More
In the modern day , hoi polloi have to examine and stay organized with 12 , mayhap even one C , of online accounts . As a result , they may fall back using well-to-do - to - think passwords out of a ill-conceived horse sense of convenience , or using the same password across multiple web site .
ByTalon Homer
In a world where digital privacy is progressively important , finding the right putz to protect your datum is substantive . With nomadic telephone becoming cardinal to our lives , it ’s crucial to select apps that prioritise secrecy .
ByJennifer Chu - Nguyen
In today ’s digital old age , safeguarding your mobile concealment is vital . Here are three easy step , powered by Startpage , to keep your digital living secure .
In the realm of online secrecy , secret hunt engines provide a carapace against intrusive tracking and data point collection . Let ’s research five big options .
In the digital world , alphanumeric characters roleplay an important part . The term " alphanumerical " encompasses both letters and number , creating a various set that forms the origination of compose language , data processor programming and secure password cosmos .
ByYara Simón
Websites like Spokeo , PeopleFinder and Intelius collect ream of data on you , your congenator , court records and other personal information . But perplex it move out is n’t so easy .
ByDave Roos
Do you have a password manager ? How about a VPN ? Here ’s why you might desire both , in the form of antivirus software , uncommitted with a discount from HowStuffWorks .
ByPartner Content From TotalAV
Private browsers and lookup engines offer much more auspices than using a even web internet browser or lookup engine , or a web internet browser with privateness modality - enabled . They can harbour your sensitive data , ward off third - political party ads and trackers , and provide a safer browsing experience .
ByMelanie Radzicki McManus
We ’re tell to change our computer passwords often , but sometimes it can be a hassle to call back how to do it . Here are some easy instructions for changing your Gmail password .
ByJeremy Glass
Some Airbnb guests have found obscure television camera in their lease homes . Is this legal ? And how can you severalize if you ’re being spied on ?
ByNathan Chandler
It may seem like you get endless alerts to refresh your Microsoft Windows system and you might be tempt to hop-skip a few update . Is there any impairment in doing that ?
rapid growth bombardment - when interloper hijack your videoconference call or virtual learning school term - has become a big deal . But how do you block off it ?
What really materialise when you transfer your internet browser to the incognito feature ? You may believe you ’re completely anonymous on the cyberspace , but that ’s not what ’s happening .
Even if you use the " incognito " setting on your web browser , your personal and search information are still being collected at an alarming rate . Private search engines and browser app calculate to diminish your digital footprint .
To what extent is U.S. news able to conduct surveillance on the internet natural action and electronic communication of U.S. citizens ?
ByJonathan Strickland&Patrick J. Kiger
datum privateness concerns have prompted some new constabulary to go into gist in the European Union - and that stand for change for consumers in the rest of the Earth too .
HowStuffWorks explains how blockchain technology , which relies upon a apportion record of transactions across a peer - to - peer connection of computers , is taking over the world .
It ’s the technology behind the meteorically rise bitcoin , and it could be really , really with child .
ByJonathan Strickland
The guy rope at Stuff They Do n’t Want You To Know babble about whether you could really cancel your internet chronicle - and why you desire to .
ByDiana Brown
It ’s sweet to have a personal assistant like Amazon ’s Alexa do your bid . Except when it does something you did n’t look to , like purchase order an lovely dollhouse .
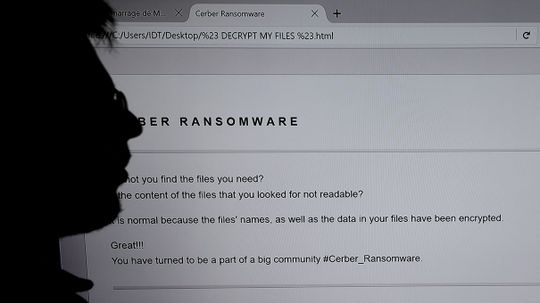
Ransomware is come for us all .
ByJulia Layton
Trolls are everywhere these days , driving people off Twitter and wreak havoc online . They also have specific personality trait that the general universe does n’t .
And the FBI already has said it ’ll aid other law enforcement office with locked phones .
ByJohn Donovan
Whether you clap their Robin Hood - style ideology of championing detached speech or hate their reckless disregard for the result of their military action , it ’s undeniable that Anonymous has become a strength to be reckoned with in late yr . From hacking politicians ' emails to taking down government website , many of the group ’s action seem to range the line [ … ] The post 9 Things Everyone Should be intimate About The Hacktivist Group Anonymous appear first on Goliath .
By Wes Walcott
The poor answer is yes . The recollective answer ? Some masses do it for mischief , others for criminal purpose , and even governance are in on the game .
ByChris Opfer