Wireless technologyseems like it ’s everywhere these days . conceive of learn a walk through a crowded area — perhaps the shopping district of a big metropolis . Maybe you ’re just doing some casual window shopping , and you ’ve kept your earpiece with you and left Bluetooth on " discoverable " modality . This allow otherBluetoothphones to locate you . As you linger in front of a shoe store and consider a new pair , your headphone beeps : Someone ’s sent you a text content . It reads : " We jazz where you are . Having playfulness shopping ? " Sounds like something out of a film , ripe ?
Such a thing is possible , and it ’s happened before . In fact , it ’s the very nature of Bluetooth — a technology that can search for and locate other devices that also have Bluetooth — which has some masses concerned . security department has long been an issue with this applied science — bluejacking , for representative , although simply a harmless prank , allow Bluetooth exploiter to send out unsolicited messages to nearby devices . Because Bluetooth devices are to some grade trackable , the construct ofBluetooth surveillancehas been precede into the technical school globe .
The phrase Bluetooth surveillance might call down up images of freehanded Brother in George Orwell ’s dystopian novel of the future , " 1984 , " but is that really the idea ? Bluetooth surveillance has a lot of benignant uses as well . To see about Bluetooth surveillance and whether or not you should remain discoverable , read on .
Bluetooth Discoverability
Before we plunge into Bluetooth surveillance , we ’ll want to take a look at how Bluetooth itself works and understand what makes the technology trackable . Bluetooth devicesuse the free2.4 - gigahertzradio frequence band known asISM , which stands for industrial , scientific and medical machine . The band is unlicensed for humble - power use of goods and services , so headsets and other Bluetooth accessories use very short in the way of batteries . Bluetooth ’s worldwide availability and low power requirements make it a very democratic criterion for connecting all kinds of equipment , from consumer electronics to business applications to equipment on the Internet of Things .
Many of the Bluetooth software we ’re most familiar with are curt - range uses , such as computing gadget peripherals , wireless headphones and connections to automotive amusement systems . Bluetooth signal can travel far , however , even more than a kilometer(three - quartern of a mi ) .
The most introductory security measure feature film on Bluetooth - enable devices is the ability to go into one of two modes : " discoverable " or " non - ascertainable . " This information is typically found in the " setting " alternative of a gadget ’s control dialog box , where you could select whether or not to make yourphoneorlaptopvisible to others within the surface area . If you want to copulate a Bluetooth keyboard to your computer , you make both equipment discoverable and take the keyboard in the computing equipment ’s Bluetooth options . It will ask you to type in a computer code expose onscreen , a security measure designed to verify that you and your information processing system agree on the correct gimmick to mate .
Simpler gadget , such aswireless headphone , do n’t necessitate a security system code when you pair them . Once the two connect , they salt away the info that identifies the other as a remember machine .
If several Bluetooth equipment are set on ascertainable mode , they all have the power to explore for and locate each other , so long as they rest within range . Every devicehas its own savoir-faire , a unparalleled 48 - bite identifierwith six bytes of information that might look like this : 01:23:45:67:89.10 . The first three byte ( 01:23:45 ) are allot to the specific manufacturer of the twist , while the last three byte ( 67:89:10 ) place the gimmick itself .
So how could someone cut through your movement if you leave behind your phone on discoverable ? Would they have to follow you around all 24-hour interval long , or is there a dim-witted mode ?
Bluetooth Positioning and Tracking
Locating several Bluetooth users with a typicalmobile phoneis relatively simple : You just turn on your phone and see which devices are discoverable in your Bluetooth configurations . But you may only supervise the people moving in and out of your Bluetooth ’s chain , which is most likely a 10 - meter ( 33 - foot ) circle around you . If you wanted to track a specific address , you ’d have to visually locate that soul ’s physical machine and follow it around all day , which would well shove along your covering fire . And locating someone else ’s smartphone does n’t have you mind in on what they ’re doing or say their email .
But If several Bluetooth - enable receivers are strategically come out to extend a large area , they can cut across the positions of any discoverable gadget , memorialise and sending any data back to a single address . Each Bluetooth receiver acts like any regular Bluetooth machine : It look for for every twist within mountain range . If a person walk down a 100 - meter - long ( 328 - foot - long ) street and each Bluetooth receiver had a range of 10 m , five receivers with a wheel spoke of 20 meters ( 66 feet ) would be needed to tail that individual ’s cause . As he walked toward the street , the first receiver would track him for the duration of the first 20 meters , the 2nd for the next 20 meters , and so on for the duration of the street .
So how have multitude used this arrangement to cut through people ? One of the earliest uses of Bluetooth locating and trailing technology is the Aalborg Zoo , the largest zoological garden in Denmark , in 2003 . The point of installing the system was not to put the menagerie ’s supporter under surveillance or to see which expo masses went to more often . Instead , special " Bluetags " were made availableto prevent parents from losing valuable belonging that be given to weave off — their children . A parent could attach a " Bluetag " onto a child , and Bluetooth receivers around the zoo would track the child ’s movement .
Bluetooth beacons ( hardware transmitters ) have become commonplace for customers to find their way around retail environment . A shopping center , for illustration , could put in a Bluetooth surveillance system throughout its full area to monitor the front of Bluetooth owner . Although it would n’t present a utterly precise description of a person ’s front , the system could create a universal map of his track and even compare how long someone stays in a sealed area .
For example , in 2018 , Bluetooth reported that the jumbo Mall of America in Minneapolis was using its engineering . " With a Bluetooth beacon infrastructure in place , Guest can select their destination on the Mall of America app and pinpoint where they are in the facility . From there , the app can get customers moving in the right direction while ply additional information , such as store hr , approximate time of comer , and vertical deportation factors like escalator clause that impact availableness for shopper utilizing perambulator or wheelchairs,“the company wrote .
You may have been using this same technology without realizing it . Personal Bluetooth trackers such asthe Tile seriesand Apple ’s AirTags are very helpful for finding things you misplace often , such as your keys . An app on your smartphone can tell you where they are , as long as they are near another Bluetooth equipment that can name the tracker . But this requires many people to have Bluetooth enable . If you leave your keys at your desk , your work neighbor ’s headphone might be capable to tell you properly where they are . They ’re doing a form of Bluetooth surveillance , and so are you — you ’ve opted into the internet of people looking for these tracker and elapse on that info to someone who may have lose something authoritative .
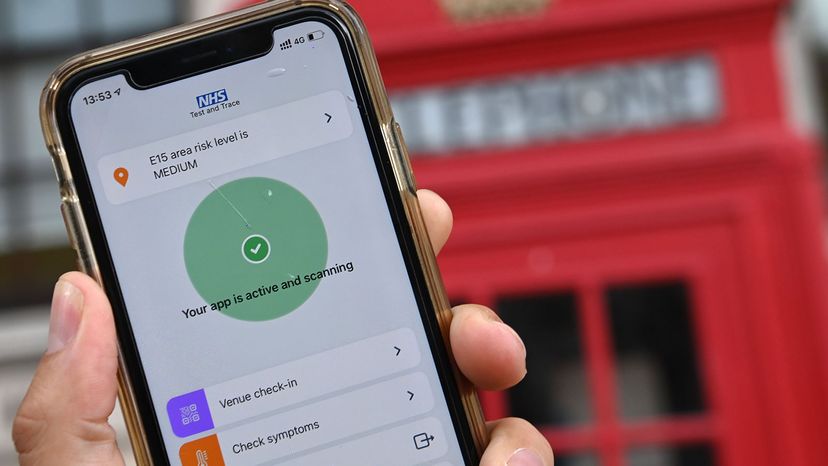
During the COVID-19 pandemic , several governments have used Bluetooth engineering in tracking equipment that citizens download on their telephone . In the case of Britain , if someone has tested positive for COVID-19 ( and the person agrees),the National Health Servicewill beam them a link where they should fill up out the contact information ( names , addresses , telephone set numbers ) of anyone they have had physical contact with . The tracing app will then alert these multitude and may propose ego - isolation depending on the type of contact . The app also lets user know if they are near someone who has test positively charged for COVID-19 .
Bluetooth Lingo
Since many terms related to Bluetooth surveillance use some variation of the Bluetooth stigma name , it helps to get a few classify out . Many touch specifically to attacks on smartphones . One of these isbluesmacking , a denial - of - service attack that sends an overwhelming amount of data dealings to the machine in an attempt to shut it down .
Bluejacking , a frivolity that involves sending fellow Bluetooth user unsolicited text messages , does n’t actually have anything to do with hijacking , even though the name implies it . The term is only a hybrid of Bluetooth and " ajack , " the username of the Malaysian IT who discovered the bug and spread the news over the cyberspace . Bluejackingis mostly an annoyance , althoughthe technique could be used in a phishing attackto convince someone to share personal data using societal engine room .
Bluesnarfing , on the other hand , happen when an attacker reads , changes or copies information from a person ’s phone , such as a headphone book , address leger or calendar . More serious infringements of bluesnarfing admit take over someone ’s phone and using it to make headphone birdsong , mail text content or surfboard the web .
Bluebuggingis an blast design to set up a backdoor on your machine . A back door is a vulnerability that allows someone else to arrive at access to your machine , like leaving the back room access undetermined in your house . A bluebugging attack can be used to gain access to your personal information or for surveillance . Key Negotiation of Bluetooth , or KNOB , exploit the data link handler communications protocol in Bluetooth to set a security samara only one byte long on gadget before they plant a connection . Someone within range can then crack theone - letter passcodeto gain access to information on the headphone or to lumber key stroke .
Discovered in 2019 , the KNOB vulnerabilityhas since been patched . If you ’ve never updated your older Bluetooth devices , you should . Even though Bluetooth tracking is mostly harmless , if you are concerned that it can violate your privacy , you should turn Bluetooth off when you ’re not using it .