Anyone who has watch theTVshow " Las Vegas " has seenfacial identification technologyin activeness . In any give episode , the security department at the fictional Montecito Hotel and Casino utilise its video surveillance organisation to pull an figure of a circuit card tabulator , thief or blacklist soul .
It then lam that effigy through the database to chance a match and distinguish the individual . By the end of the hr , all regretful cat are see from thecasinoor throw in jail . But what count so easy on television does n’t always translate as well in the real world .
Humans have always had the innate power to recognize and recognise between faces , yet computer only recently have show the same power . In the mid 1960s , scientists lead off usingcomputersto greet human faces . Since then , facial recognition software has add up a long way .
Here , we will look at the story of face acknowledgement technology , the changes that are being made to heighten their capabilities and how governments and private companies expend ( or contrive to use ) them .
Facial Recognition Technology
Identix ® , a society base in Minnesota , was one of many former developers of facial realization system . Its software , FaceIt ® , could pick someone ’s look out of a crowd , pull up the aspect from the rest of the scenery and compare it to a database of put in figure .
In gild for this software to work , it had to know how to differentiate between a basic grimace and the rest of the background . A face identification system is base on the power to recognize a face and then mensurate the various features of the face .
Every boldness has numerous , distinct landmark : the different tiptop and vale that make up facial feature . FaceIt defined these turning point as nodal degree . Each human face has about 80 nodal points . Some of the ones mensurate by the package were :
FaceIt used these measured nodal points to make a numeric code , called a faceprint , symbolise the face in the database .
In the past times , front recognition organisation relied on a 2D image to liken or identify another 2D effigy from the database . To be efficient and accurate , the persona get needed to be of a face that was looking almost directly at the camera , with piddling variance of light or facial expression from the image in the database .
This created quite a trouble .
In most instance the images were not taken in a controlled surround . Even the smallest changes in twinkle or orientation could deoxidize the effectiveness of the organisation , so they could n’t be matched to any face in the database , leading to a eminent rate of failure . In the next section , we will look at ways to correct the problem .
3D Facial Recognition
A comparatively new trend in facial recognition technology uses a 3D model , which lay claim to furnish more truth .
Capturing a real number - time3D imageof a person ’s facial surface , 3D facial identification identifies the subject by using classifiable features of the face — where rigid tissue paper and bone is most apparent , such as the curve of the eye socket , nose and chin . These areas are all unique and do n’t deepen significantly over time .
Using depth and an axis of measurement that is not feign by firing , 3D facial realisation can even be used in swarthiness and has the power to recognise a subject at different view angles with the potential to recognize up to 90 degrees ( a side in visibility ) .
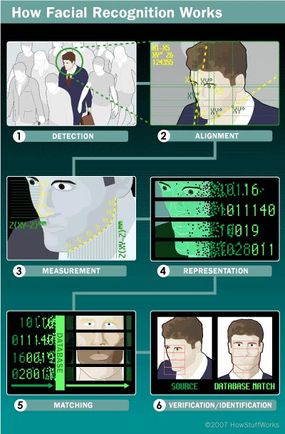
Using the 3D computer software , the system goes through a series of stone’s throw to assert the indistinguishability of an individual .
Detection
acquire an icon can be execute by digitallyscanningan existing photograph ( 2D ) or by using a video persona to acquire a bouncy picture of a subject ( 3D ) .
Alignment
Once it detects a face , the facial identification organisation determines the point ’s place , size of it and pose . As stated earlier , the content has the potential to be realize up to 90 grade , while with 2D , the head must be turned at least 35 level toward thecamera .
Measurement
The system then measure the curves of the cheek on a sub - millimeter ( or microwave oven ) plate and creates a template .
Representation
The organisation translates the templet into a unique computer code . This coding gives each template a Seth of numbers to represent the features on a matter ’s face .
Matching
If the image is 3D and the database check 3D image , then matching will take topographic point without any changes being made to the image . However , there is a challenge currently facing databases that are still in 2D images .
3D provides a live , moving variable subject being compared to a flat , stable image . New facial recognition engineering science is addressing this challenge . When a 3D image is taken , different points ( usually three ) are identified .
For example , the outside of the optic , the interior of the eye and the bakshish of the nose will be pulled out and mensurate . Once those mensuration are in place , analgorithm(a step - by - whole step procedure ) will be applied to the image to exchange it to a 2D image .
After conversion , the package will then compare the image with the 2D simulacrum in the database to find a likely compeer .
Verification or Identification
In check , an image is match to only one range of a function in the database ( 1:1 ) . For example , an image taken of a subject area may be rival to an image in the Department of Motor Vehicles database to verify the subject is who he says he is .
If recognition is the goal , then the image is compared to all paradigm in the database , result in a score for each potential match ( 1 : N ) . In this instance , you may take an image and equate it to a database of mug shots to describe who the topic is .
Next , we ’ll look at how cutis biostatistics can help avow match in facial acknowledgment technology .
Biometric Facial Recognition
The open grain psychoanalysis ( STA ) algorithm operates on the top pct of results as influence by the local feature depth psychology . STA creates a skinprint and performs either a 1:1 or 1 : N mates , depending on whether you ’re looking for verification or identification .
The image may not always be aver or identified in facial realization alone , so Identix ® created another merchandise to help with precision . FaceIt ® Argus used skinbiometrics , the uniqueness of skin grain , to yield even more accurate results .
The process , called Surface Texture Analysis , work much the same agency facial identification does . A characterization is ask of a patch of cutis , call a skinprint . That patch is then break up into small blocks .
Using facial recognition algorithmic rule to flex the plot of ground into a numerical , measurable space , the system would then distinguish any line , pore and the literal skin texture . It could key out differences between superposable Gemini the Twins , which had not been possible using facial realisation software system alone .
FaceIt used three dissimilar templates to corroborate or identify the subject : vector , local feature analysis and surface texture depth psychology .
By coalesce all three guide , FaceIt ® offered an vantage over other facial acknowledgment systems .
It was comparatively insensitive to change in saying — including nictate , frowning or smiling — and had the ability to compensate for mustache or beard growth and the appearance ofeyeglasses . The organisation was also consistent with regard to subspecies and grammatical gender .
However , it was not a perfect system . There were some factor that could get in the way of credit , including :
While most facial recognition system shape the same way FaceIt does , there are some mutation . For example :
Due to these stride in engineering , modern facial acknowledgement system of rules are more widely used than they were just a few long time ago . In the next section , we ’ll reckon at where and how they are being used and what ’s in stock for the future .
Facial Recognition Systems Uses
In the past , the elemental exploiter of facial recognition engineering science have been law enforcement agency , who used the system to capture random cheek in crowds . Now , other government agency are getting in on the action .
Immigration
In the early 2000s , the U.S. government begin a broadcast called US - VISIT ( United States Visitor and Immigrant Status Indicator Technology ) , aimed at foreign travelers realize unveiling to the United States . When a alien traveller receive his visa , they reconcile fingerprints and have their photograph taken .
The fingerprint and picture are check against a database of lie with criminals and distrust terrorists . When the traveler get in the United States at the port of entrance , those same fingerprint and photographs will be used to verify that the person who received the visa is the same individual seek to derive entry .
Traveling
As facial recognition systems become less expensive , their use becomes more far-flung . They are now compatible with cameras and computers that are already in manipulation by banks and airport .
Time Tracking
A4Vision , a creator of facial credit technology , is presently marketing a system that will keep track of employees ' time and attendance . Their vane website states that it will prohibit " brother punching , " which will cut down on security measure risks and decreased productivity .
Finance
Other possible program includeATMand chip - cashing security measure . The software system is able to apace swear a customer ’s face . After a customer consent , the ATM or chip - cashing kiosk captures a digital image of him . The software then generate a faceprint of the photograph to protect customer against identicalness thieving and fraudulent transactions .
By using the facial recognition software , there ’s no need for a picture ID , bankcard or personal recognition number ( PIN ) to swan a customer ’s identity . This way line can preclude fraud from fall out — or , if it does , law enforcement government agency can swiftly answer .
But , of row , there ’s also a risk of false negatives in this scenario : What if the computer software does n’t recognize you trying to access your own history ? No one wants to be interlock out of access their own John Cash .
Concerns About Privacy in Facial Recognition Systems
While all the illustration above work with the permission of the individual , sometimes the use offacial recognitionis done without a person ’s consent or noesis . opponent of the systems note that while the technology does leave protection in some instances , it is not enough to justify overriding a gumption of liberty and exemption .
Many feel that privacy infringement is too great with the use of these systems , but their concerns do n’t terminate there . They also point out the risk involved withidentity stealing . Even facial identification corporations admit that the more use the technology gets , the higher the likelihood of identity thieving or fraud .
As with many develop applied science , the incredible potential of facial recognition comes with some drawbacks , but manufacturer are striving to heighten the usability and accuracy of the systems .