Key Takeaways
Has your computer ever become so slow that you may prepare yourself a snack in the time it accept your Book processor to open ? Perhapsspywareis to pick .
Spyware is a family of estimator programs that attach themselves to youroperating systemin nefarious ways . They can blow the life out of your computer ’s processing power . They ’re designed to track your Internet habits , nag you with undesirable sales offers or generate traffic for their legion entanglement land site . According to some estimates , more than 80 percent of all personal computers are infect with some kind of spyware [ source : FaceTime Communications ] . But before you chuck your data processor out the window and move to a desert island , you might want to read on . In this clause we ’ll explicate how spyware gets install on your computer , what it does there and how you’re able to get free of it .
Some the great unwashed mistake spyware for a estimator virus . Acomputer virusis a piece of computer code design to reduplicate itself as many times as potential , spread from one host information processing system to any other computers connect to it . It unremarkably has a loading that may damage your personal files or even your operating organisation .
At present , most spyware object only theWindows operating system . Some of the more infamous spyware menace include Trymedia , Nuvens , Estalive , Hotbar and New . nett . demesne . Plugin [ source : CA ] .
How Your Computer Gets Spyware
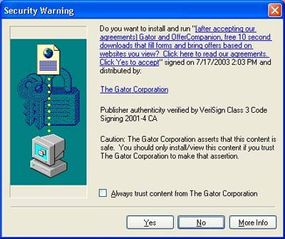
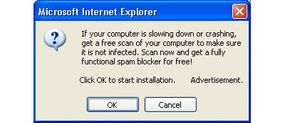
Spyware commonly end up on your machine because of something you do , like click a push on a belt down - up windowpane , installing a software program package or agreeing to add together functionality to your Web web browser app . These applications often use trickery to get you to install them , from fake system alert messages to button that say " cancel " when they really put in spyware . Here are some of the general ways in which spyware finds its manner into your computer :
What Spyware Can Do
Spyware can do any numeral of thing once it ’s instal on your computer .
At a minimum , most spyware runs as an app in the background as presently as you commence your computer up , hoggingRAMand central processing unit index . It can generate endless pop - up ads that make your WWW internet browser so slow it becomes unusable . It can readjust your web browser app ’s home page to exhibit an ad every time you open it . Some spyware redirects your vane search , controlling the results you see and making yoursearch enginepractically useless . It can also modify the dynamically yoke libraries ( DLLs ) your computer uses to connect to the Internet , causing connectivity failures that are hard to diagnose . At its very worst , spyware can record the words you typecast , your web browsing story , password and other private information .
sure types of spyware can modify your net options so that if you connect through telephone dial - up overhaul , yourmodemdials out to expensive , pay telephony figure . Like a spoiled client , some spyware changes yourfirewallsettings , inviting in more undesirable pieces of software system . There are even some bod that are sassy enough to know when you attempt to withdraw them in the Windows register and intercept your attempts to do so .
Another use of spyware is to slip affiliate credit . Major shopping sites likeAmazonandeBayoffer credit to a Web site that successfully direct traffic to their item page . sure spyware practical software capture your requests to consider sites like Amazon and eBay and then take the cite for sending you there .
Legality
So is it legal to install unmanageable - to - dispatch software without the user ’s permit ? Not really . There ’s an increase physical structure of res publica legislation that explicitly bans spyware , including theSpyware Control Actin Utah and theConsumer Protection Against Computer Spyware Actin California . But even without these new state law , Union law already prohibits spyware . TheComputer Fraud and Abuse Actcovers any unauthorized package instalment . delusory barter practice session of any kind also violate theFederal Trade Commission Act . Additionally , theElectronic Communications Privacy Actmakes it outlaw for party to outrage the security of customers ' personal information .
Just likeanti - spam lawmaking , these spyware laws can be very difficult to enforce in practice , and the perpetrators know it . It can be tough to find hard evidence connecting item-by-item ship’s company to their spyware products , and , as with all Internet - colligate lawsuit , there are often battle over which royal court ’s legal power applies to the case . Just because it ’s illegal does n’t signify it ’s easy to stop .
How can you protect yourself against spyware , and what can you do if you believe you already have some on your computer ? Here are a few suggestions .
Use a spyware scanner.
There are several software you’re able to bend to for trusty spyware detection and remotion , includingAd - aware , SpybotandMicrosoft AntiSpyware , which is presently in beta . All three are free for the personal edition . These work just like your anti - virus computer software and can provide active protective cover as well as detection . They will also detectInternet cookiesand tell you which seat they refer back to .
Note - Once you have it away which spyware is on your information processing system , in some case you ’ll need to search specific instructions on how to remove it . link to some of those instruction are list in the " Spyware Help " box seat to the right , and more are included in the Lots More Information section at the destruction of this clause . Here are a few more solutions :
Use a pop-up blocker.
Many of the current browsers , including Internet Explorer 6.0 and Mozilla Firefox 1.0 , have the power to kibosh all Web site from serve you pop - up windows . This routine can be configured to be on all of the sentence or to alert you each time a site wants to pop up a new windowpane . It can also tell apart you where the pop - up is coming from and selectively give up windows from sure sources .
Disable Active-X.
Most browsers have certificate preferences in their preferences which admit you to specify which actions Web sites are allowed to take on your machine . Since many spyware program take reward of a special codification in Windows called Active - ex , it ’s not a bad idea to merely handicap Active - X on your browser app . notice that if you do this , you will also disallow the legitimate consumption for Active - X , which may interfere with the functionality of some Web sites .
Be suspicious of installing new software.
In universal , it pays to be suspicious when a site ask to install something new on your computer . If it ’s not a male plug - in you acknowledge , like Flash , QuickTime or the latest Java railway locomotive , the secure plan of action is to reject the induction of new components unless you have some specific grounds to hope them . Today ’s Web sites are sophisticated enough that the huge majority of functionality happens inside your web browser , ask only a stark lower limit of standard nag - IN . Besides , it never hurts to refuse the induction first and see if you could get on without it . A trustworthy land site will always give you the chance to go back and download a needed component by and by .
Use the “X” to close pop-up windows.
Get to know what your computer ’s arrangement subject matter reckon like so that you’re able to tell apart a fake . It ’s usually jolly easy to tell the difference once you get to know the standard look of your system alerts . Stay away from the " No thanks " button if you may help it , and instead end the window with the default " X " at the recession of the toolbar . For an even more reliable selection , use the key stroke compounding for " airless window " build into your software system . you may search in your web browser ’s " File " menu to obtain it .
For more information on spyware , spyware remotion and related topics , check out the link on the next pageboy .