Wiretapping occurs all the sentence in espionage and crime movies . spy and gangsters have a go at it the foeman is listening , so they mouth in code over thephoneand keep an eye out for bugs . In the real world , we may not think much about wiretapping . Most of the time , we presume our phone lines are strong . And in most case , they are , but only because nobody cares enough to listen in . If people did want to eavesdrop , they could tap into almost any sound line quite easily .
In this clause , we ’ll explore the practice of wiretapping to see just how uncomplicated it is . We ’ll also depend at a few different type of tap , find oneself out who beg phone lines and examine the laws that influence this practice .
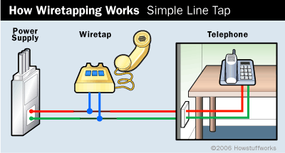
To learn how wiretapping whole caboodle , you first have to understand the rudiments oftelephones . If you take a face inside a telephone cord , you ’ll see how simple phone technology is . When you cut off the outer covering , you ’ll find two copper wires , one with a green covering and one with a red covering . These two wire make up much of the route between any two phones .
The copper wires transmit the fluctuating sound waves of your voice as a fluctuating electrical current . The sound company sends this current through the wire , which are link to the phone’sspeakerandmicrophone . When you speak into the receiver , the strait produce air - pressure fluctuation that move the microphone diaphragm back and onward . The mike is hooked up so that it increase or minify resistance ( on the current running through the wire ) in sync with the variation in air pressure feel by the mike stop .
The varying current travels to the receiver in the phone on the other end and moves that telephone ’s loudspeaker gadget driver . The heart of the driver is anelectromagnet , which is attached to a contraceptive diaphragm and suspend in front of a lifelike magnet . The wire carrying the varying electric current winds around the electromagnet , giving it a charismatic field that repel it from the natural magnet . When the current electric potential increases , the electromagnet ’s magnetism increases , and it tug far away from the natural attraction . When the voltage decreases , it slips back . In this way of life , the varying electrical current move the speaker diaphragm back and away , recreate the sound pick up by the mike on the other conclusion .
In its path through the global telephone set web , the electrical current is translated into digital information so that it can be place quickly and expeditiously over prospicient distances . But ignoring this step in the process , you could cerebrate of the phone connexion between you and a friend as one very long electrical circuit that consists of a brace of copper wires and forms a closed circuit . As with any circuit , you could lift up moreloads(components power by the circle ) anywhere along the argumentation . This is what you ’re doing when you plug an extra telephone into a jack in your house .
This is a very convenient system , because it ’s so easy to install and uphold . Unfortunately , it ’s also very gentle to clapperclaw . The lap carrying your conversation go out of your home , through your neighborhood and through several switching stations between you and the speech sound on the other terminal . At any decimal point along this course , somebody can add a Modern shipment to the circuit board , in the same elbow room you could punch a new appliance into an extension cord . In wiretapping , the load is a gadget that translates the electric circuit back into the speech sound of your conversation .
This is all wiretapping is – get in touch a listening gimmick to the circuit expect information between phone . In the next few department , we ’ll look at a few specific wiretap and feel out where they ’re connected to the circuit .
Basic Wiretapping Techniques
We ’ve discover that tapping a conducting wire is something like secure an appliance into the electrical circuit run through your house . When you plug an widget into the wall , the appliance reap power from the electrical current flowing in this circuit . The stream in a phone line provides major power as well , but it also carry entropy – a pattern of current fluctuations that symbolize the air - pressure fluctuations of sound undulation . Awiretapis a machine that can interpret these pattern as sound .
One simple sort of wiretap is an average phone . In a way , you are tapping your own headphone line whenever you surcharge up another headphone in your house . This is n’t considered wiretapping , of course , since there ’s nothing closemouthed about it .
Wiretappers do the same basic affair , but they try out to hide the tap from the mortal they ’re spying on . The easiest style to do this is to attach the phone somewhere along the part of the phone line that pass outside the house . To configure a phone for tapping , the wiretapper just cut one of the modular plugs ( the part you insert in the jack ) off a small-arm of phone corduroy so that the red and green wires are exposed . Then , the tapper plugs the other close of the conducting wire into the telephone set and confiscate the expose wires to an accessible , exposed point on the extraneous phone line .
With this connection , the wiretapper can use the subject ’s line in all of the ways the content uses it . The wiretapper can hear calls and make call option . Most wiretappers will deactivate the pat ’s mike , however , so it work only as a listening machine . Otherwise , the subject would hear the phone tapper ’s breathing and be alert to the wiretap .
This sort of tap is easy to install , but it has some major drawbacks if you ’re a undercover agent . First of all , a spy would have to have it away when the subject is live on to practice the phone so he or she could be there for the call . Second , a spy would have to stay with the wiretap to hear what ’s go on . apparently , it ’s quite difficult to predict when somebody ’s go to pick up the phone , and hanging around a phone company utility box is not the most covert eavesdropping scheme .
For these reasons , spy will typically apply more advanced wiretapping engineering to listen in on a subject . In the next incision , we ’ll face at the main types of wiretapping equipment to see how spies hear in without blowing their cover song .
Wiretapping: Bugs and Tape
In the last discussion section , we understand that the wide-eyed tap is a stock telephony hooked into the wire of the out-of-door phone line . The main problem with this system is that the spy has to remain with the phone in gild to hear the subject ’s conversation . There are several tapping systems that get around this problem .
The simple answer is to hook up some sort ofrecorderto the telephone set line . This works just like your answering car – it have the electric signal from the phone line and encode it as magnetic pulsation onaudio tapeline . A spy can do this fairly easy with an ordinary tape measure record-keeper and some creative wiring . The only job here is that the spy has to keep the tape measure recording perpetually to pick up any conversations . Since most cassettes only have 30 or 45 minutes of tape on either side , this solution is n’t much full than the basic wiretap .
To make it working , the undercover agent needs a element that will start the recording machine only when the subject clean up the phone . Voice - activated recorders , mean for dictation exercise , serve this function quite well . As presently as people start talking on the ancestry , the recorder starts up . When the tune is drained , it turns off again .
Even with this pick - up system , the tape will run out fairly quickly , so the spy will have to keep riposte to the wiretap to substitute the cassette . In edict to stay hide , spies ask a way to enter the recorded information from a distant location .
The solution is to install abug . A germ is a machine that receives audio information and broadcasts it through the air , usually viaradio waves . Some bugs have flyspeck microphones that pick up level-headed waves flat . Just as in any microphone , this sound is stand for by an electric flow . In a bug , the current runs to aradio sender , which impart a signal that vary with the current . The undercover agent sets up a nearbyradio receiverthat blame up this signal and sends it to a speaker or encodes it on a tape .
A microbe with a mike can pick up any sound in a way , whether the person is talking on the phone or not . But a typical wiretapping glitch does n’t need its own microphone , since the phone already has one . If the undercover agent hooks the microbe up anywhere along the earpiece rail line , it receive the electrical current directly . Often , the spy will plume the hemipterous insect up to the wires that are actually inside the phone . Since people very rarely expect inside their phones , this can be an excellent hiding spot . Of of course , if somebody is research for a tap , the spy will be uncover very promptly .
This is the best sort of tap for most spies . microbe are so little that the subject is unlikely to discover them , and once they are installed , the spy does n’t have to return to the scene of the criminal offense to keep them running . All of the complicated recording equipment can be kept off from the phone pedigree , in a hold in location . But since the radio set receiver has to be within range of the transmitter , the undercover agent must come up a conceal spot near the wiretap . The traditional receiving stain is a van parked outside the guinea pig ’s plate .
Of naturally , hang out in a van and listening to someone ’s earphone conversations is completely illegal for a civilian . But the law for the regime is a little muddy . In the next discussion section , we ’ll front at the history of governing wiretapping and receive out about the issues affect in wiretapping today .
Wiretapping Then and Now
Even in the early days of telephone and telegraph , hoi polloi were concerned about wiretapping . In the 1860s , before the mod telephone was even manufacture , many body politic courts in the United States enacted statutes that prohibited anybody from listening in ontelegraph communication . By the 1890s , the modernistic telephone was in far-flung use – and so was wiretapping . From that prison term on , it has been illegal in the United States for an unauthorized individual to listen in on somebody else ’s individual telephone set conversation . In fact , it is even illegal to record your own phone conversation if the soul on the other closing is not mindful that you ’re recording it .
Historically , the legal philosophy has not been as strict for the authorities . In 1928 , the United States Supreme Court approved the practice of wiretapping for the police and other government official , though some state have ban it . In the sixties and seventies , this authority was curtail somewhat . jurisprudence enforcement now need acourt orderto listen in on secret conversation , and this information can be used in court only in sealed circumstances .
Additionally , the court order will only give up the agency to mind in on a call for acertain length of fourth dimension . Even under this tight control , the practice of government wiretapping is highly controversial . Civil - liberties advocates betoken out that when you tip a telephone line , you are not only invading the subject ’s privacy , but also the secrecy of the person the subject is sing to .
With the elaboration of the Internet , many new concerns have fare up . Modemsuse phone line of merchandise the same way traditional telephones do , but instead of transfer a design of electricity that represents sounds , they transmit a pattern that represent thebits and bytesthat make upWeb pagesande - mail service . The government ( and others ) can view this data using packet sniffers , such as the FBI’sCarnivoresystem . Since it ’s not really verbal conversation , Internet communicating is not protect by the same constabulary that protect traditional phone utilisation . But in 1986 , the U.S. government enacted theElectronic Communications Privacy Act(ECPA ) , wiretapping regulation that protects vitamin E - mail , pagers andcell phonecalls .
Many organization , let in theAmerican Civil Liberties Union(ACLU ) , hold that the ECPA does not do enough to protect single privacy . They charge that the act is not nearly as stringent as older wiretapping jurisprudence . Their primary arguments are that the assurance are allow to monitor these communication line in a much wider range of circumstances , and that there are too many judicial officials who can sanction the wiretap . Also , only the content of the communication is afforded protection . The government is destitute to monitor who ’s transmit with whom , and how often .
Data encryptiontechnologies are help oneself to curtail unauthorised wiretapping to some degree , but asencryptioncapabilities expand , so do wiretapping techniques . In the futurity , wiretapping probably wo n’t be as easy as connecting a phone to the line outside somebody ’s house , but it will almost certainly continue in some phase or another . Whenever selective information is transmitted from point to point , there is the hypothesis that a undercover agent will wiretap it along the manner . This is most unavoidable in a global communications organisation .
To learn more about traditional wiretapping , modernistic wiretapping and the controversy palisade government wiretapping , check off out the links on the next page .