What is an IP address?Every machine on a meshing has a unique identifier . Just as you would address a letter to send in the mail , computers use the unequaled identifier to send data to specific computing machine on a internet .
Most meshwork today , including all computing machine on theinternet , use the TCP / IP protocol as the banner for how to communicate on the meshing . In the TCP / IP protocol , the unique identifier for a computer is phone its IP address .
There are two standard for IP addresses : IP Version 4 ( IPv4 ) and IP Version 6 ( IPv6 ) . All computers with IP address have an IPv4 destination , and most habituate the new IPv6 address organisation as well . Here are the differences between the two address types :
At the dawn of IPv4 addressing , the internet was n’t the gravid commercial sensation it is today , and most networks were private and shut off from other networks around the man . When the cyberspace exploded , having only 32 chip to identify a unequalled cyberspace destination caused concerns that we ’d run out of IP addresses before long .
Under IPv4 , there are 232 potential combinations , which offer just under 4.3 billion unique addresses . IPv6 raised that to a tension - relieving 2,128 possible addresses . Later , we ’ll take a closer look at how to empathize your figurer ’s IPv4 or IPv6 addresses .
How Computers Get IP Addresses
An IP reference can be either dynamic or static . A static address is a permanently assigned address . A still IP address that is ascribe by an cyberspace service supplier is rare . you may assign inactive IP name and address to devices on your local internet , but it can make internet issues if you use it without a respectable agreement of TCP / IP .
Dynamic IP name and address are the most rough-cut . They ’re attribute by the active Host Configuration Protocol ( DHCP ) , a armed service running on the internet . DHCP typically runs on internet ironware such asroutersor consecrate DHCP server .
A dynamic IP address is issue using a leasing system , have in mind that the IP destination is only active for a special metre . If the letting pop off , the computing machine will automatically call for a new lease . Sometimes , this means the computer will get a new IP address , too , especially if the electronic computer was disconnect from the connection between leases .
This process is usually transparent to the exploiter unless the computer warns about an IP address difference of opinion on the electronic web ( two computers with the same IP address ) . An address engagement is rare , and today ’s engineering science typically sterilize the problem automatically .
Next , let ’s take a tightlipped looking at the important parts of an IP address and the special roles of certain addresses .
IP Classes
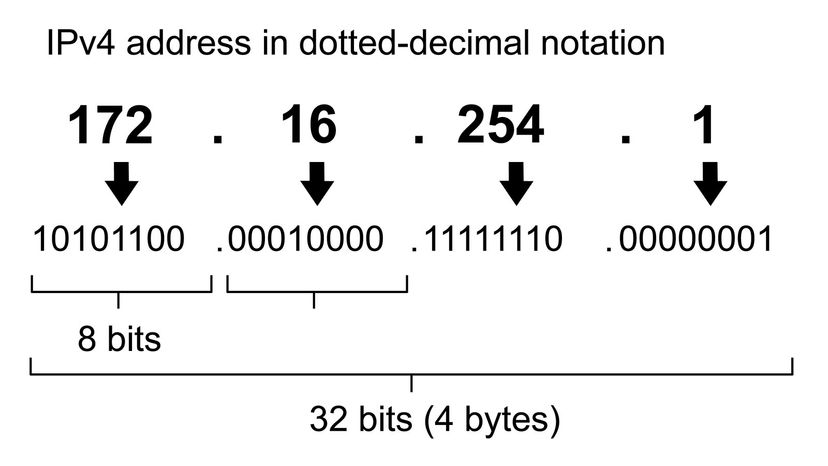
Earlier , you read that IPv4 address represent four eight - figure binary numbers . That intend that each figure could be 00000000 to 11111111 in binary , or 0 to 255 in denary ( base-10 ) . In other words , 0.0.0.0 to 255.255.255.255 .
The other IP address qualification are for subnet classes . A subnetwork is a smaller connection of reckoner connected to a larger meshing through a router . The subnet can have its own savoir-faire system so information processing system on the same subnet can pass on promptly without post data across the bombastic internet .
A router on a TCP / IP net , including the cyberspace , is configure to recognize one or more subnets and route connection dealings suitably . The succeed are the IP addresses set aside for subnets :
The first three ( within Classes A , atomic number 5 and century ) are those most used in creating subnets . Later , we ’ll see how a subnet uses these speech . The IANA has outlined specific uses for multicast addresses within internet Engineering Task Force ( IETF ) document RFC 5771 . However , it has n’t point a aim or next program for Class atomic number 99 speech since it reserved the blocking in its 1989 document RFC 1112 . Before IPv6 , the internet was filled with debate about whether the IANA should release Class E for general enjoyment .
Next , let ’s see how subnets exercise and find out who has those non - reserved IP address out on the internet .
Internet Addresses and Subnets
The following is an example of a subnet IP address you might have on your figurer at home if you ’re using a router ( wireless or wired ) between your ISP connection and your computer :
Besides hold IP addresses , the IANA is also responsible for assign blocks of IP savoir-faire to sealed entity , normally commercial or government organizations . Your cyberspace serving supplier ( ISP ) may be one of these entity , or it may be part of a larger block under the mastery of one of those entity . When you connect to theinternet , your ISP depute you one of these addresses . you could see a full listing of IANA assignment and arriere pensee for IPv4 address at IANA ’s website [ germ : IANA ] .
If you only plug in one computer to the net , that computing machine can use the address from your ISP . Many homes today , though , use router to share a single net connection between multiple computers .
If you employ a router to share an internet connecter , the router gets the IP address issued immediately from the ISP . Then , it creates and manages a subnet for all the computers connected to that router . If your calculator ’s speech fall into one of the reserve subnet mountain chain listed earlier , you ’re hold up through a router rather than connecting directly to the internet .
informatics addresses on a subnet have two parts : connection and lymph node . The web part identifies the subnet itself . The node , also call the legion , is an individual small-arm of computer equipment join to the connection and requiring a unique address . Each reckoner knows how to separate the two parts of the IP address by using a subnet mask . A subnet mask wait somewhat like an IP computer address , but it ’s actually just a filter used to determine which part of an IP address designates the internet and node [ seed : Solarwinds ] .
A subnet mask consists of a serial publication of 1 bite followed by a series of 0 number . The 1 bits indicate those that should dissemble the mesh routine in the IP address , revealing only those that identify a unique leaf node on that web . In the IPv4 standard , the most commonly used subnet masks have unadulterated eighter from Decatur of 1s and 0s as follow :
People who go down up big networks determine what subnet mask work comfortably ground on the number of desire subnets or nodes . For more subnets , utilise more bits for the mesh ; for more node per subnet , use more bits for the node . This may entail using non - standard masquerade values . For example , if you need to use 10 bits for networks and 22 for nodes , your subnet mask note value would require using 11000000 in the second octet , resulting in a subnet mask economic value of 255.192.0.0 .
Another important thing to mention about IP addresses in a subnet is that the first and last addresses are set aside . The first savoir-faire discover the subnet itself , and the last computer address identifies the broadcast computer address for organisation on that subnet .
Understanding Private and Public IP Addresses
Learning to make out between private and public IP addresses is important too . These classifications serve different purpose , both of which are fundamental to how devices communicate over the internet and within local internet [ root : Mitchell ] .
Allocation and Registration
On the other hand , individual IP addresses are not registered or controlled by a central self-confidence . They are allocated for use within private networks , like those found in homes , schools , and offices .
Accessibility and Scope
As mentioned above , a public IP address is approachable over the internet , which makes them essential for external internet communication . They are assigned to devices that postulate to be direct accessible from outside the local web . This includes things like World Wide Web servers , electronic mail servers , and routers that connect a local web to the web .
A private IP reference permit multiple gadget within the same web to transmit with each other . These addresses ca n’t be get at directly from outside the connection .
Security and Cost
The public nature of public IP reference necessitates careful management . Firewalls , encroachment detection systems , and other security department standard are often necessary to protect devices with public IPs from unauthorized access by security threats .
Again , individual IP addresses run on a closed circuit , which creates a level of isolation that makes them safer . Moreover , since private IPs are freely uncommitted and reusable in different net , they serve conserve the limited supply of public IP addresses and repress costs for organizations and individuals .
The Role of IP Addresses in Digital Communication
Few construct are as central to modern communicating as the internet protocol computer address . IP addresses enable equipment from all over the globe to find and communicate with one another in the blinking of an eye ! Despite how far the net has descend , IP addresses stay essential cogs that turn on the roulette wheel of the internet to stay on moving .
As you ’ve learned , an IP address is a cardinal element that underpin the connectivity and functionality of our digital earthly concern . And , by take out the nature and function of IP addresses , we not only profit a deeper perceptiveness for the mechanic at child’s play , but also empower ourselves to voyage and mold the communications landscape with more confidence .